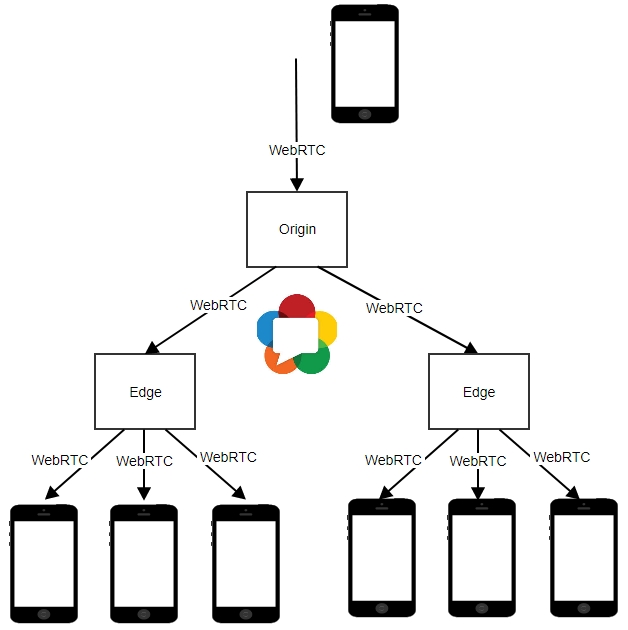
In this article, let’s see in detail how to set up a STUN/TURN server for WebRTC communication. Before stepping into it, let us discuss in detail what is WebRTC, STUN, TURN and how are they linked with one another.
What is WebRTC?
WebRTC (Web Real-Time Communication) is a technology that allows Web browsers to stream audio or video media, as well as to exchange random data between browsers, mobile platforms, and IoT devices without requiring an intermediary.
WebRTC allows web applications to run features like:
1. Video Conferencing
2. File Sharing
3. Screen Sharing
4. Broadcasting etc.
In real-time communication, a Video Gateway has to be deployed over the Internet so any user must connect and send media fragments over RTP (Real-time Transport Protocol) ports without having specific issues.
But sometimes this would not be sufficient because there are possibilities where some users might face connectivity issues because of different IP networks where Firewalls and NATs (Network Address Translators) could include specific network policies that will not allow RTC communications.
In order to solve this kind of network connection scenario, we need to use ICE (Interactive Connectivity Establishment) protocol and it defines a systematic way of finding possible communication options between a peer and the Video Gateway (WebRTC).
ICE (INTERACTIVE CONNECTIVITY ESTABLISHMENT) is a protocol used to generate media traversal candidates that can be used in WebRTC applications, and it can be successfully sent and received through Network Address Translation (NAT)s using STUN and TURN.
What is STUN?
STUN (Session Traversal Utilities for NAT) that complements ICE through NATs using UDP protocol. STUN allows applications to discover the presence and types of NATs and firewalls between them and on the public Internet. It can be used by any device to determine the IP address and port allocated to it by a NAT.
Typically A STUN client can send messages to the STUN server to get the Public IP and ports information then STUN server retrieve that information. Using this Public IP and Port information clients will make a peer to peer communication through the internet.
What is TURN?
TURN (Traversal Using Relays around NAT) is a protocol that assists in the traversal of network address translators (NAT) or firewalls for webRTC applications. TURN Server allows clients to send and receive data through an intermediary server. The TURN protocol is the extension to STUN.
In a few cases, client communication endpoints are stuck behind different types of NATs, or when a symmetric NAT is in use, it may be easier to send media through a relay server and its called the TURN server.
Typically A TURN client first sends a message to a TURN server to allocate an IP address and port on the TURN server. Once the allocation has succeeded, the client will use the IP address and port number to communicate with peers. The TURN packet contains the destination address of the peer, then converts these packets as the UDP protocol packet and sends this to the peer.
TURN is most useful for Web, Mobile and IoT clients on networks masqueraded by symmetric NAT devices. But the TURN server cost is high because of the server utilization and huge bandwidth usage in the case where more client connections are established.
Setup STUN/TURN server using Coturn
Here you can find the following steps to install and configure the Coturn server.
Step 1: Firewall rules to Open ports:
First, make sure to open the following ports in the firewall or Cloud security Groups.
3478 TCP & UDP
49152–65535 UDP
Step 2: Coturn installation
Coturn can be installed directly from the Ubuntu package repositories, so install it with the following command.
$ sudo apt-get update
$ sudo apt-get install coturn
Step 3: Start the Coturn Daemon at Startup
To let it auto-start at system boot time, modify /etc/default/coturn file.
sudo nano /etc/default/coturn
Find the following line and uncomment it by removing the # to run Coturn as an automatic system service daemon.
#TURNSERVER_ENABLED=1
Save and close the file. And you can then start the Coturn service by running.
$ systemctl start coturn
Step 4: Create a TURN user to Next, edit the main configuration file.
Then open or create /etc/turnserver.conf file and paste the following content. Replace <USERNAME>, <PASSWORD> and <PUBLIC_IP_ADDRESS> values with your respective ones.
fingerprint
user=<USERNAME>:<PASSWORD>
lt-cred-mech
realm=tensorbugs.in
log-file=/var/log/turnserver/turnserver.log
simple-log
external-ip=<PUBLIC_IP_ADDRESS>
Here you can find the below example of my own sample details for your references.
fingerprint
user=madhukaran:123456
lt-cred-mech
realm=tensorbugs.in
log-file=/var/log/turnserver/turnserver.log
simple-log
external-ip=103.155.12.18
Step 5: Restart the Coturn Service
you can restart the service using the following command.
$ sudo service coturn restart
Step 6: Testing Time
Go to the Trickle ICE page and enter your own TURN server details.
Testing fo r the STUN/TURN Server can be done on the bellow following Links:
1. Trickle Ice
If you test a STUN server, it works if you can gather a candidate with type "srflx". If you test a TURN server, it works if you can gather a candidate with type "relay".
If you test just a single TURN/UDP server, this page even allows you to detect when you are using the wrong credential to authenticate.
STUN or TURN URI: turn:<PUBLIC_IP_ADDRESS>:3478
TURN username: <USERNAME>
TURN password: <PASSWORD>
Some Result for reference,
Then click Add Server and then “Gather candidates” button. If you have configured everything correctly, you should see “Done” as the final result.